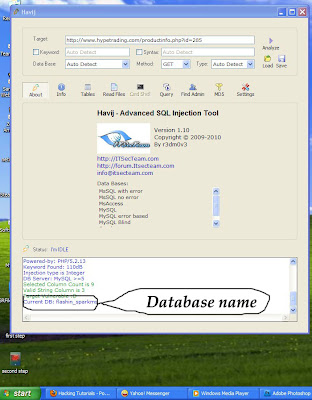
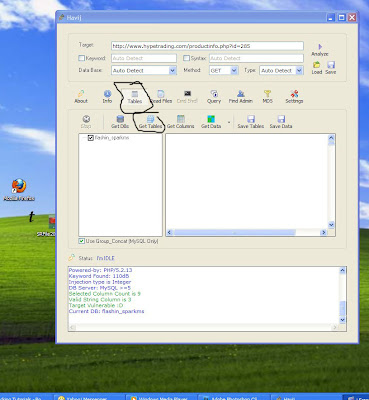
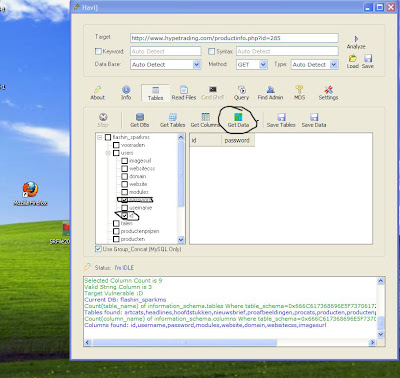
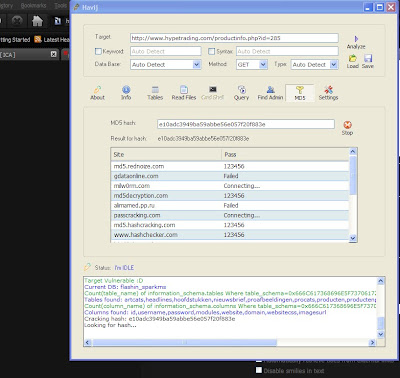
What was this case about?
The Legion of Doom (LOD) was a hacker group active from the 1980s to the late 1990s and early 2000. Their name appears to be a reference to the antagonists of Challenge of the Superfriends. LOD was founded by the hacker Lex Luthor, after a rift with his previous group the Knights of Shadow.
At different points in the group's history, LOD was split into LOD and LOD/LOH (Legion of Doom/Legion of Hackers) for the members that were more skilled at hacking than pure phreaking. The overall beliefs of LOD and MOD were different, but it can be difficult to untangle the actions of the members since there was a cross-overs between the two groups.
Who were the parties involved?
As of 2012 what has happened to each individual member of the Legion of Doom is unknown. A small handful of the higher-profile LOD members who are accounted for includes: "Erik Bloodaxe", "Mark Tabas", "Karl Marx", "Agrajag the Prolonged", "Automatic Jack", "Bill From RNOC", "Lord Digital", "The Mentor", "Doctor Who", "Dead Lord", "Phiber Optik", who was a member of both LOD and Masters of Deception (MOD), and "Terminus".
Did any prosecution results? If so what where there outcomes?
"'Hacker' Pleads Guilty in AT&T CASE: Sentence Urged for Md. Man Among Stiffest Yet for Computer Crime"
By Mark Potts/Washington Post Staff Writer
BALTIMORE, March 22--A computer "hacker" "Legion of Doom" who was trying
to help others steal electronic passwords guarding large corporate computer
systems around the country today pleaded guilty to wire fraud in a continuing
government crackdown on computer crime.
Federal prosecutors recommended that Leonard Rose Jr., 32, of
Middletown, Md., be sent to prison for one year and one day, which
would be one of the stiffest sentences imposed to date for computer
crime. Sentencing is scheduled for May before U.S. District Judge J.
Frederick Motz.
What Ethical Issues are raised by this case?
One way that people can interpret actions for unethical behavior is considering the legality. In United States for an instance which has Credit Fraud and Abuse Act prohibits intentionally accessing another`s computer system when it threatens the financial well-being of an individual or business to reveal state secrets, upset international communications, defraud, cause damage or aid extortion. States have their own laws as well.
Other points considered in discussions of ethical hacking include the costs associated with security checks even when no alterations or damages have occurred. Many consider the high amount of adolescent participants and factor this into ethical judgments, believing the anonymity associated with hacking makes crimes more likely to happen than they would outside of cyberspace